So I've found myself in need of some Android network sniffing. Well that's an easy one.
What we need
- A device with Android >= 4.0 and tcpdump.
- Or: An emulator with Android >= 4.0.
- Android development tools.
- WireShark.
Let's do it
This method is much easier done using an emulator, because these come with tcpdump preinstalled and grabbing the captured traffic out of an emulator is a piece of cake.
First of all we need to install WireShark.
On the emulator
- List your available virtual devices:
emulator -list-avds - Start an emulator with tcpdump:
emulator -tcpdump {DUMP_FILE_LOCATION} -avd {AVD_NAME} - Run your app and do your thing.
- Close the emulator.
- Start WireShark.
- Drag and drop your capture file into WireShark.
Example
C:\Users\Nitz>emulator -list-avds
Nexus_5X_API_22
Nexus_5X_API_22_64bit
C:\Users\Nitz>emulator -engine classic -tcpdump d:\dump.cap -avd Nexus_5X_API_22_64bit
emulator: WARNING: Classic qemu does not support SMP. The hw.cpu.ncore option from your config file is ignored.
emulator: device fd:1372
HAXM is working and emulator runs in fast virt mode
emulator: Listening for console connections on port: 5554
emulator: Serial number of this emulator (for ADB): emulator-5554
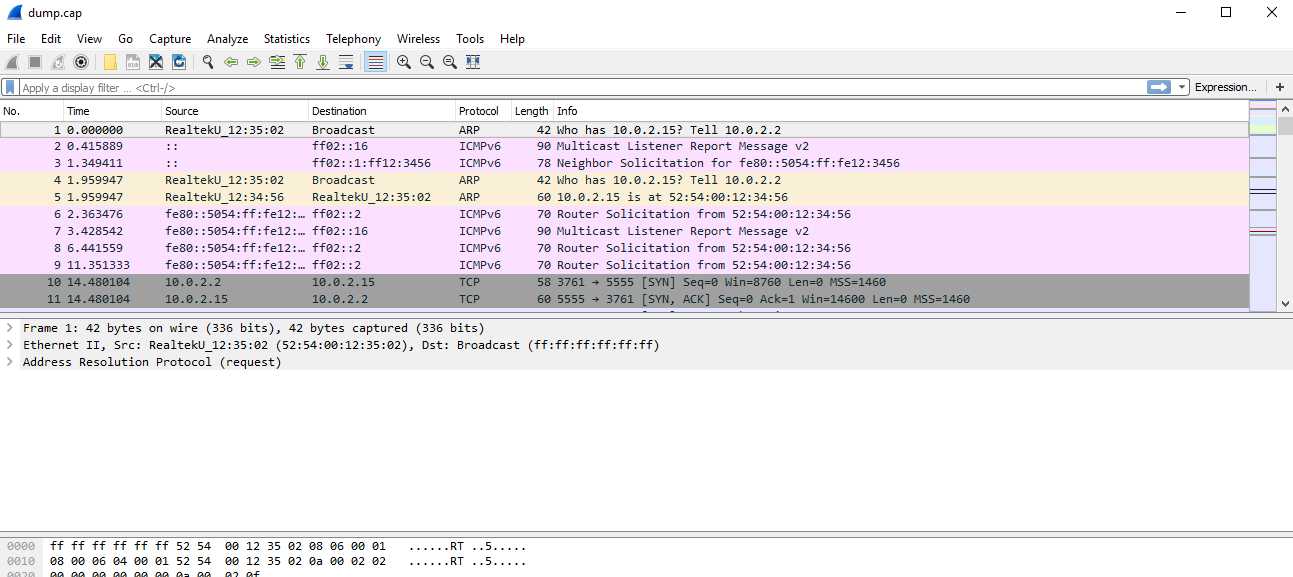
And the result:
On a real device
- First root your device. This will not be explained here of course.
- Assuming an ARM device, grab the latest tcpdump from here.
If your device is x86, you may need to cross-compile manually. This is explained here and here. - Push tcpdump into your rooted device:
adb push tcpdump /system/xbin/ - Let's test:
adb shell tcpdump -h
Should result in something like this:
libpcap version 1.6.1
Usage: tcpdump [-aAbdDefhHIJKlLnNOpqRStuUvxX] [ -B size ] [ -c count ]
[ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ]
[ -i interface ] [ -j tstamptype ] [ -M secret ]
[ -P in|out|inout ]
[ -r file ] [ -s snaplen ] [ -T type ] [ -V file ] [ -w file ]
[ -W filecount ] [ -y datalinktype ] [ -z command ]
[ -Z user ] [ expression ]
- Now let's start tcpdump for all available interfaces:
adb shell tcpdump -i any -p -s 0 -w /sdcard/capture.pcap - Press ctrl-c when done.
- Pull the captured traffic out of the device:
adb pull /sdcard/capture.pcap . - Run WireShark.
- Drag and drop the captured network file to WireShark.
What about SSL?
In order to parse SSL traffic we'd need to set up a MITM proxy. We've talked about this in this post.